Encryption is a reversible process, whereas hashing is one-way only. Data that has been encrypted can be decrypted back to the original value. Data that has been hashed cannot be transformed back to its original value. Encryption is used to protect sensitive information like Social Security Numbers, credit card numbers or other sensitive information that may need to be accessed at some point. Hashing is used to create data signatures or comparison only features. For example, user passwords … [Read more...] about What is the difference between encryption and hashing?
application security
Ep. 118: Log4J Sparking Thought on Vulnerable Components
Log4J has been the talk of the town recently and everyone is focused on the technical details of the specific vulnerabilities found. In this episode, James talks about the overarching ideas around dealing with vulnerable components. Are you vulnerable? If so, what needs to be done? Listen to the Episode: For more info go to https://www.developsec.com or follow us on twitter (@developsec). … [Read more...] about Ep. 118: Log4J Sparking Thought on Vulnerable Components
Log4J – Reflection and Progression
Open any social media platform or pull up any mainstream media and undoubtably, you have seen many posts/articles talking about the log4j vulnerability. If you haven't seen this, here is a quick link to catch up https://snyk.io/blog/log4j-rce-log4shell-vulnerability-cve-2021-4428/. This post is not going to be about log4j, nor is it going to go into any of the details the thousands of others articles out there would go through. Instead, I want to discuss this at a higher level. Log4j is just an … [Read more...] about Log4J – Reflection and Progression
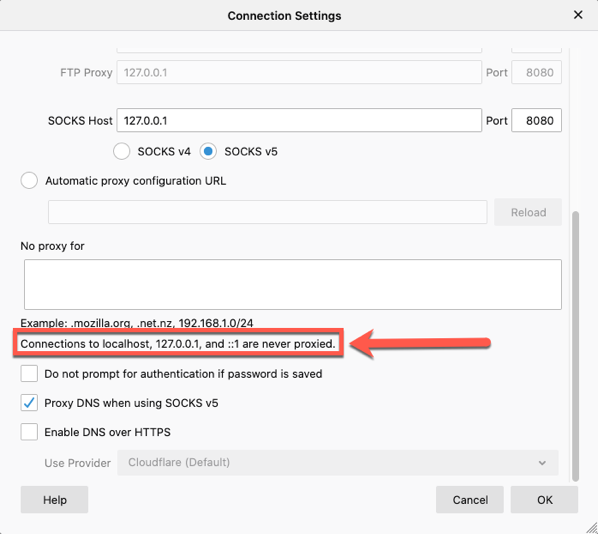
Proxying localhost on FireFox
When you think of application security testing, one of the most common tools is a web proxy. Whether it is Burp Suite from Portswigger, ZAP from OWASP, Fiddler, or Charles Proxy, a proxy is heavily used. From time to time, you may find yourself testing a locally running application. Outside of some test labs or local development, this isn't really that common. But if you do find yourself testing a site on localhost, you may run into a roadblock in your browser. If you are using a recent version … [Read more...] about Proxying localhost on FireFox
Chrome is making some changes.. are you ready?
Last year, Chrome announced that it was making a change to default cookies to SameSite:Lax if there is no SameSite setting explicitly set. I wrote about this change last year (https://www.jardinesoftware.net/2019/10/28/samesite-by-default-in-2020/). This change could have an impact on some sites, so it is important that you test this out. The changes are supposed to start rolling out in February (this month). The linked post shows how to force these defaults in both FireFox and Chrome. In … [Read more...] about Chrome is making some changes.. are you ready?
Ep. 117: How Browsers are Helping with Security
Browsers play a role in web application security, but where does their responsibility stop and the developer's start? In this episode, we are going to discuss a few changes happening in the Chrome browser, that change security by default. Listen to the Episode: SameSite Default Chrome has announced a few changes that we need to watch out for in the near future. We previously talked about the default value for samesite that is coming up fast. I wrote about this here: … [Read more...] about Ep. 117: How Browsers are Helping with Security