Application security, like any facet of security, is a complex challenge with a mountain of solutions. Of course, no one solution is complete. Even throwing multiple solutions will never get 100% coverage. The push today is around devsecops, or pushing left in the SDLC. I am seeing more solutions recommending also pushing right in the SDLC. I feel like we are stuck at this crossroad where the arrow points both ways. The good news is that none of these recommendations are wrong. We do need to … [Read more...] about Investing in People for Better Application Security
developer training
Understanding Your Application Platform
Building applications today includes the use of some pretty impressive platforms. These platforms have so much built in capability, many of the most common tasks are easily accomplished through simple method calls. As developers, we rely on these frameworks to provide a certain level of functionality. Much of which we may never even use. When it comes to security, the platform can be a love/hate relationship. On the one hand, developers may have little control over how the platform handles … [Read more...] about Understanding Your Application Platform
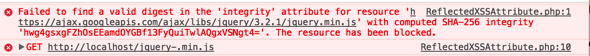
Sub Resource Integrity – SRI
Do you rely on content distribution networks or CDNs to provide some of your resources? You may not consider some of your resources in this category, but really it is any resource that is provided outside of your server. For example, maybe you pull in the jQuery JavaScript file from ajax.googleapis.com rather than hosting the file on your server. These CDNs provide a great way to give fast access to these resources. But how do you know you are getting the file you expect? As an … [Read more...] about Sub Resource Integrity – SRI
Security Tips for Copy/Paste of Code From the Internet
Developing applications has long involved using code snippets found through textbooks or on the Internet. Rather than re-invent the wheel, it makes sense to identify existing code that helps solve a problem. It may also help speed up the development time. Years ago, maybe 12, I remember a co-worker that had a SQL Injection vulnerability in his application. The culprit, code copied from someone else. At the time, I explained that once you copy code into your application it is now your … [Read more...] about Security Tips for Copy/Paste of Code From the Internet
Understanding the “Why”
If I told you to adjust your seat before adjusting your mirror in your car, would you just do it? Just because I said so, or do you understand why there is a specific order? Most of us retain concepts better when we can understand them logically. Developing applications requires a lot of moving pieces. An important piece in that process is implementing security controls to help protect the application, the company, and the users. In many organizations, security is heavily guided by an … [Read more...] about Understanding the “Why”
Ep. 1: Introduction to the Podcast
Hey everyone, I have spent a lot of time working in application security and prior to that, development. Over the years, I have had a chance to reflect a bit on some of the security issues I saw as a developer and as a security practitioner. In an effort to help share some of this knowledge and experience, I am starting a podcast series focused on secure development. The goal is for shorter, 10-20 minute, episodes. I hope you take a moment to take a listen. Transcript: Hi, and welcome to … [Read more...] about Ep. 1: Introduction to the Podcast